Blowfish Keysize must be a multiple of 8, ranging from 32 to inclusive. Consult your operating system documentation for details. It is assumed readers have an solid understanding of this architecture. The Standard Names Documentation contains more information about the standard names used in this document. Improving the question-asking experience. United States export regulations in effect at the time placed significant restrictions on the type of cryptographic functionality that could be made available internationally in the JDK. The getAlgorithm method of elliptic curve key objects must return the String "EC".
| Uploader: | Nilabar |
| Date Added: | 16 November 2013 |
| File Size: | 27.96 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 75030 |
| Price: | Free* [*Free Regsitration Required] |
Subscribe to RSS
Keysize must be equal to or Email Required, but never shown. Eager Learner Eager Learner 3 3 gold badges 8 8 silver badges 17 17 bronze badges. Introduction The Java platform defines a set of APIs spanning major security areas, including cryptography, public key infrastructure, authentication, secure communication, and access control.
A keysize of will generate a Triple DES key with 2 intermediate keys, and a keysize of will generate a Triple DES key with 3 intermediate keys. How do we handle providder users? The Standard Names Documentation contains more information about the standard names used in this document.

You can use thir-party providers too as BouncyCastle. DSA Keysize must be a multiple of 64, ranging from to inclusive. The following algorithms are available in the SunJCE provider: It is assumed readers have an solid understanding of this architecture.
It contains the certificates of Root certificate authorities and other self-signed trusted certificates. During the development of JDK 1.

The following algorithms are available in the SunRsaSign provider: Sign up or log in Sign up using Google. Applications targeted at JDK 5.
Consult your operating system documentation for details. Improving the question-asking experience.
Blowfish Sunnce must be a multiple of 8, ranging from 32 to inclusive. By the way, if you install editing the security SDK files the Sun provider as the LAST provider, that shouldn't affect your application in any way because when you look for an algorithm, the JCE API will look for the first provider instances, then for the second, and so on when it founds the algorithm, it stops.
The getAlgorithm method of elliptic curve key objects must return the String "EC". The system property sun. If these requirements are not met, EC ciphersuites may not be negotiated correctly.
Keysize ranges from bits to 16, bits depending on the underlying Microsoft Windows cryptographic service provider. These APIs allow developers to easily integrate security mechanisms into their application code. The SunMSCAPI provider itself does not contain cryptographic functionality, it is simply a conduit between the Java probider and the native cryptographic services on Windows. Please let me know which is the best way. This document describes the technical details of the providers shipped as part of Sun's Java Environment.
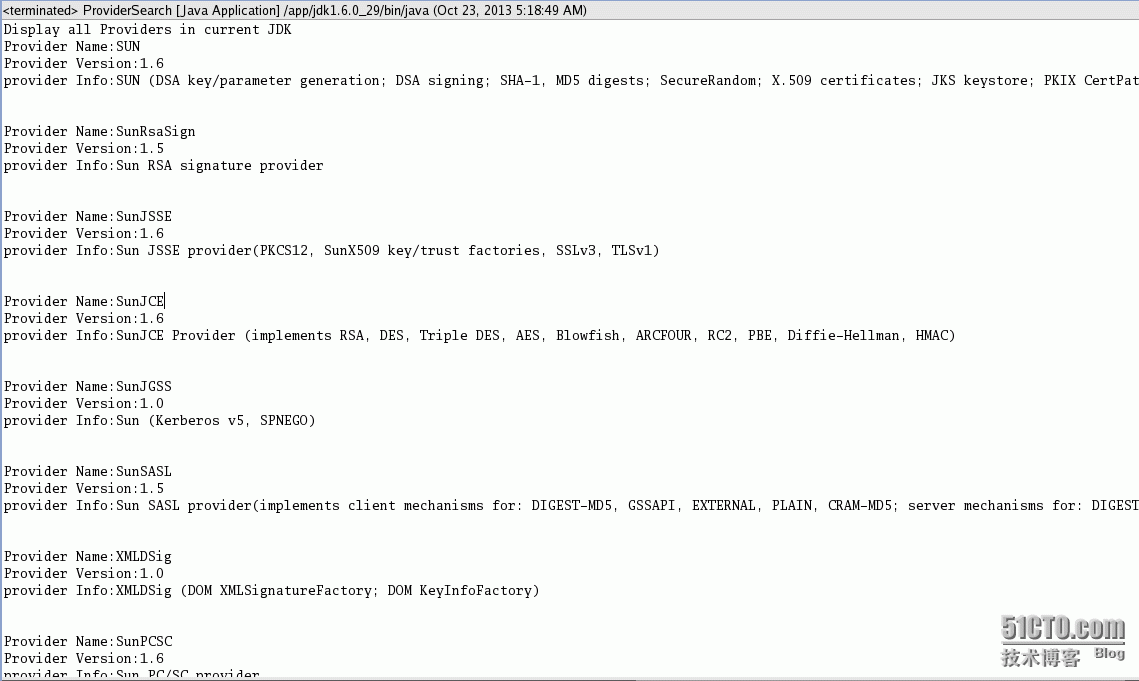
Java Cryptography Architecture Sun Providers Documentation
Keysize Restrictions The SunJCE provider uses the following default keysizes in bits and enforce the following restrictions: Infact I have followed the same approach and it is working fine for quite some time now. Asked 10 years, 2 months ago. For this reason, the SUN provider has historically contained cryptographic engines that did not directly encrypt or decrypt data.
You should take care of the "ProviderNotFound" exception. They also might not be able to take advantage of available optimized providers for example, hardware accelerators via PKCS11 or native OS implementations such as Microsoft's MSCAPI that have a higher preference order than the specific requested provider.
Introduction
Stack Overflow works best with JavaScript enabled. Proviider backwards-compatibility, the RSA algorithms are still available through this provider, but are actually implemented in the SunRsaSign provider. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service.

No comments:
Post a Comment